tech-blogs
| 🔖 | Cracking the Code: Insecure Direct Object References (IDOR) |
|---|---|
 |
|
| Insecure Direct Object References (IDORs) are a sneaky web vulnerability. They let attackers access unauthorized data by manipulating URLs or forms. This exposes sensitive information and can lead to data breaches. Understanding IDORs is crucial for building secure web applications. | |
Jan 3, 2025 4:19:07 PM • • • Powered by AI ⚙️ |
| 🔖 | Digital Camouflage: Unveiling the Art of Network Cloaking |
|---|---|
 |
|
| Network cloaking masks online identities and activities. It’s used for privacy, security, and bypassing restrictions. Techniques include VPNs, proxies, and Tor. Risks include legal issues and potential misuse. | |
Jan 3, 2025 4:30:28 PM • • • Powered by AI ⚙️ |
| 🔖 | Stealthy Invaders: Understanding Rootkits |
|---|---|
 |
|
| Rootkits are malicious software designed to hide their presence on a system. They grant attackers persistent access, often enabling further malicious activity. Detection is difficult, requiring advanced techniques. Understanding rootkits is crucial for cybersecurity. | |
Jan 3, 2025 4:36:31 PM • • • Powered by AI ⚙️ |
| 🔖 | Framejacking: Sneaky Website Hijacking |
|---|---|
 |
|
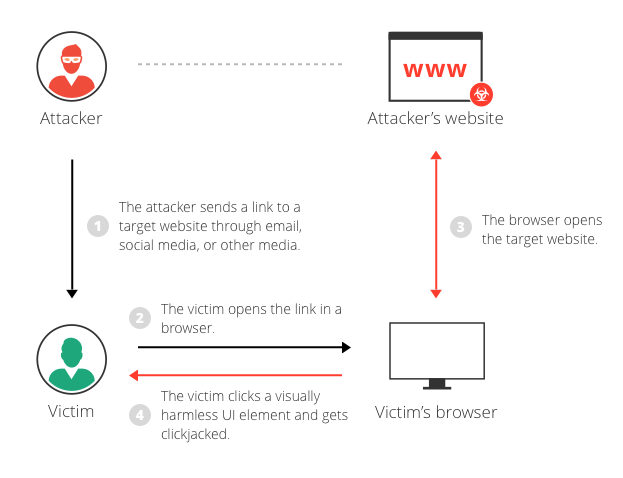
| Framejacking, a sneaky web attack, hides malicious content within a legitimate website’s frame. Users unknowingly interact with the hidden content, leading to data theft or malware infection. Understanding framejacking helps users protect themselves online. Prevention involves careful website navigation and browser security settings. | |
Jan 3, 2025 4:40:07 PM • • • Powered by AI ⚙️ |
| 🔖 | Website Cloaking: The Art of Digital Disguise |
|---|---|
 |
|
| Website cloaking presents different content to different visitors. This technique is used for SEO, A/B testing, or even malicious purposes. Understanding how it works is crucial for both web developers and cybersecurity professionals. It’s a powerful tool, but ethically and legally questionable when misused. | |
Jan 3, 2025 4:58:37 PM • • • Powered by AI ⚙️ |
| 🔖 | Remote Access Trojans: Sneaky Backdoors to Your System |
|---|---|
 |
|
| Remote Access Trojans (RATs) are malicious programs granting unauthorized remote access to a victim’s computer. They’re stealthy, dangerous, and used for various nefarious purposes, from data theft to system control. Understanding RATs is crucial for cybersecurity awareness. This article explains how they work and what to watch out for. | |
Jan 3, 2025 7:19:27 PM • • • Powered by AI ⚙️ |
| 🔖 | Web Cache Poisoning: Sneaky Attacks on Your Browser |
|---|---|
 |
|
| Web cache poisoning tricks your browser into displaying a fake website. Attackers manipulate cached data, redirecting users to malicious sites. This can steal credentials or install malware. Prevention involves strong DNSSEC and HTTPS. | |
Jan 4, 2025 2:03:38 PM • • • Powered by AI ⚙️ |
| 🔖 | DLL Side-Loading: A Stealthy Attack Vector |
|---|---|
 |
|
| DLL side-loading is a sneaky attack where malicious code is injected via a legitimate DLL. Attackers exploit search order vulnerabilities to replace or add harmful DLLs. This grants them unauthorized access and control. Understanding this technique is crucial for robust security. | |
Jan 6, 2025 1:19:34 PM • • • Powered by AI ⚙️ |
| 🔖 | Fileless Malware: The Ghost in the Machine |
|---|---|
 |
|
| Fileless malware hides in your system's memory, leaving no trace on your hard drive. It's incredibly stealthy, making detection difficult. This article explores how it works, its dangers, and methods for prevention. Understanding fileless threats is crucial for modern cybersecurity. | |
Jan 6, 2025 2:32:12 PM • • • Powered by AI ⚙️ |
| 🔖 | Cracking the SMB Code: Exploiting Server Message Block |
|---|---|
 |
|
| Server Message Block (SMB) vulnerabilities are a major cybersecurity threat. Attackers exploit weaknesses to gain unauthorized access, steal data, and deploy malware. Understanding SMB's function and its security risks is crucial for network protection. This article explores common SMB exploits and mitigation strategies. | |
Jan 8, 2025 12:57:48 PM • • • Powered by AI ⚙️ |
| 🔖 | Sneakily Injecting Code: Understanding XSS Attacks |
|---|---|
 |
|
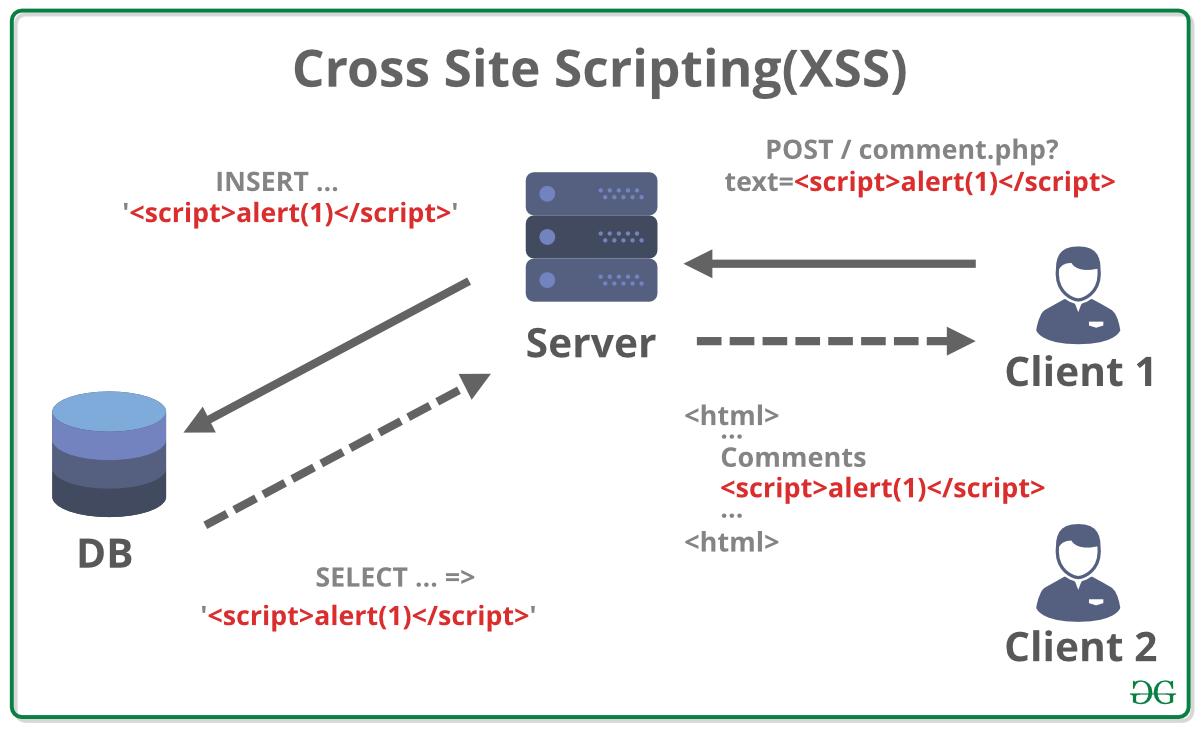
| Cross-site scripting (XSS) attacks inject malicious scripts into websites. Users unknowingly execute these scripts, compromising their data. Prevention relies on input validation and output encoding. Understanding XSS is crucial for web security. | |
Jan 9, 2025 11:47:07 AM • • • Powered by AI ⚙️ |
| 🔖 | Malware, Viruses, Trojans: Understanding the Cyber Threats |
|---|---|
 |
|
| This article differentiates between malware, viruses, and Trojans – three common cyber threats. Understanding their unique characteristics is crucial for effective cybersecurity. We'll explore their functionalities and provide real-world examples. Learn how to protect yourself! | |
Jan 11, 2025 1:48:07 PM • • • Powered by AI ⚙️ |
| 🔖 | Cracking the Code: True vs. Fake Randomness in Encryption |
|---|---|
 |
|
| Encryption relies on strong keys. This article explores the crucial difference between truly random and pseudo-random key generation, highlighting their security implications and practical applications. Understanding this distinction is vital for robust cybersecurity. | |
Jan 12, 2025 3:58:44 AM • • • Powered by AI ⚙️ |
| 🔖 | Rice's Theorem: The Undecidability of Program Behavior |
|---|---|
 |
|
| Rice's Theorem fundamentally limits what we can automatically determine about programs. It proves the undecidability of non-trivial properties of program behavior. This has significant implications for static analysis and automated security tools. Understanding this theorem is crucial for realistic expectations in cybersecurity. | |
Jan 12, 2025 7:49:38 PM • • • Powered by AI ⚙️ |
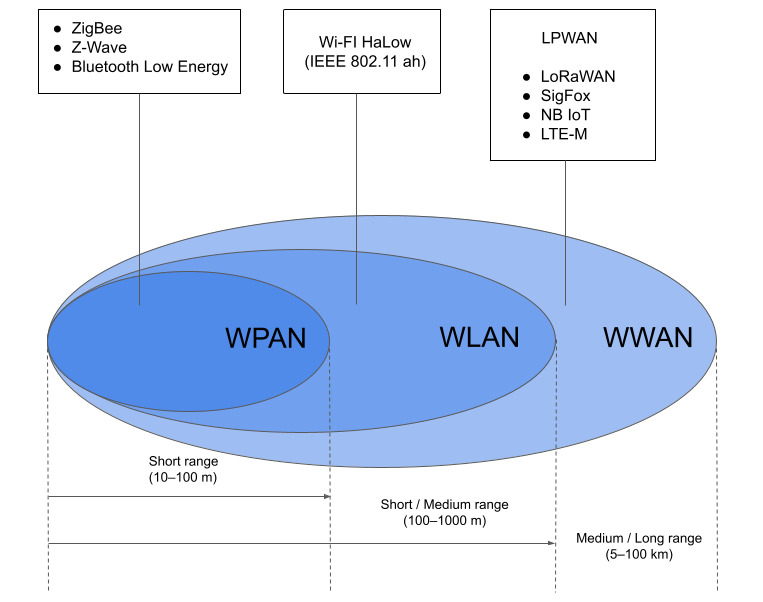
| 🔖 | Bluetooth: Short-Range Ninja vs. Long-Range Spy |
|---|---|
 |
|
| Bluetooth Low Energy (BLE) and Long Range Bluetooth (Long Range) offer distinct advantages and vulnerabilities. Understanding their differences is crucial for security. This article explores their strengths, weaknesses, and implications for cybersecurity. We’ll examine potential attack vectors and mitigation strategies. | |
Jan 17, 2025 4:27:51 AM • • • Powered by AI ⚙️ |
| 🔖 | Cracking the Code: Understanding Rainbow Tables |
|---|---|
| Rainbow tables are pre-computed lists used to crack password hashes. They speed up the process significantly. This article explains how they work and their implications for security. Understanding rainbow tables helps in implementing better password security practices. | |
Jan 19, 2025 1:39:11 AM • • • Powered by AI ⚙️ |
| 🔖 | Cracking the Code: Understanding CUPP – The Password Profiler |
|---|---|
 |
|
| CUPP, the Common User Password Profiler, is a powerful tool used in penetration testing to generate likely passwords. It leverages publicly available information to create realistic password guesses. This helps assess password security vulnerabilities. Understanding CUPP is crucial for improving your security posture. | |
Jan 19, 2025 2:12:38 PM • • • Powered by AI ⚙️ |
| 🔖 | Unleash the Power of Google Dorking: A Hacker's Secret Weapon |
|---|---|
 |
|
| Google Dorking leverages advanced Google search operators to uncover sensitive information. It's a powerful tool for ethical hackers and security researchers. Learn how to use it responsibly and ethically. This article provides a comprehensive guide and case studies. | |
Jan 25, 2025 3:27:17 AM • • • Powered by AI ⚙️ |
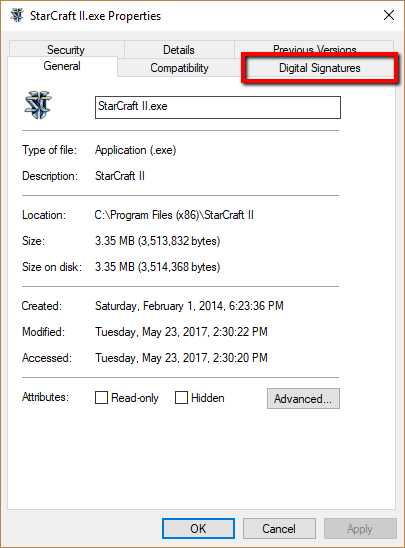
| 🔖 | Decoding Digital Signatures: Trusting Your Executables |
|---|---|
 |
|
| Digital signatures verify software authenticity. They ensure executables haven't been tampered with. This protects users from malware. Trusting only signed software enhances security. | |
Jan 25, 2025 3:36:43 AM • • • Powered by AI ⚙️ |
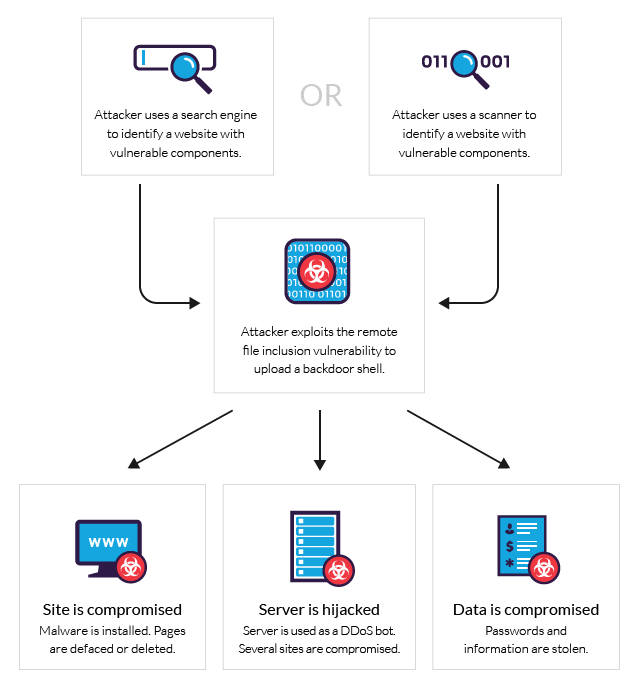
| 🔖 | Sneaky Local Files: Understanding LFI Vulnerabilities |
|---|---|
 |
|
| Local File Inclusion (LFI) vulnerabilities allow attackers to access files on a web server. This is done by manipulating URLs to include local files. Exploiting LFIs can reveal sensitive data or even allow remote code execution. Understanding LFI is crucial for web security. | |
Jan 27, 2025 3:22:06 AM • • • Powered by AI ⚙️ |
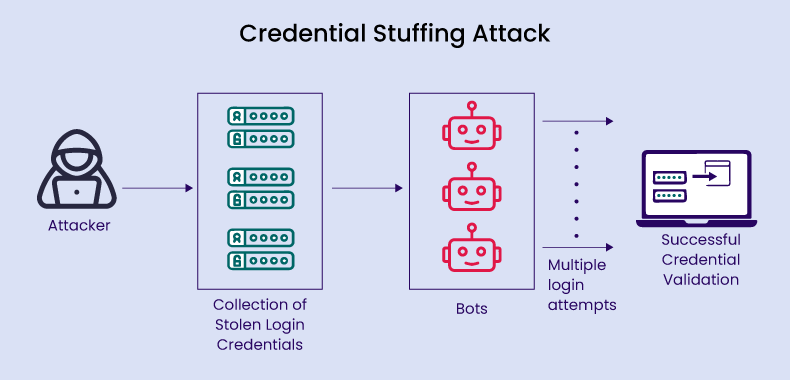
| 🔖 | Credential Stuffing: The Brute-Force Bandit of the Internet |
|---|---|
 |
|
| Credential stuffing automates login attempts using leaked usernames and passwords. It's a common attack exploiting reused credentials. This article explains how it works, its impact, and how to protect against it. Prevention relies on strong passwords and multi-factor authentication. | |
Jan 30, 2025 12:32:57 AM • • • Powered by AI ⚙️ |
| 🔖 | Sneaky Side Channels: Cracking Codes Without the Key |
|---|---|
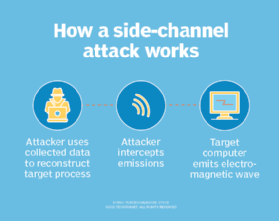 |
|
| Side-channel attacks exploit information leaked during computation, not weaknesses in the algorithm itself. They target timing, power consumption, or even electromagnetic emissions. This bypasses traditional cryptographic defenses. Understanding these attacks is crucial for robust security. | |
Jan 30, 2025 12:45:36 AM • • • Powered by AI ⚙️ |
| 🔖 | Bloatware: The Silent Thief of Your Device's Performance |
|---|---|
 |
|
| Bloatware – pre-installed apps slowing your device. These unwanted programs consume resources, create vulnerabilities, and impact privacy. Learn how to identify and remove them for a faster, safer device. Protecting your digital life starts here! | |
Jan 30, 2025 9:15:21 AM • • • Powered by AI ⚙️ |
| 🔖 | Deceptive Scareware: Don't Fall for the Digital Fear! |
|---|---|
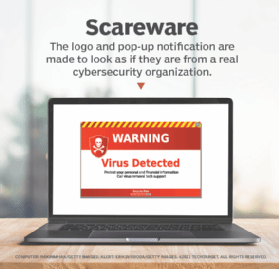 |
|
| Scareware uses fear to trick you. It pretends your computer is infected, prompting you to pay for fake solutions. This malicious software is a common cyber threat. Learn how to identify and avoid it. Protect your data! | |
Feb 7, 2025 11:46:20 AM • • • Powered by AI ⚙️ |
| 🔖 | Decoding the Phishing Trap: How to Spot and Avoid Online Scams |
|---|---|
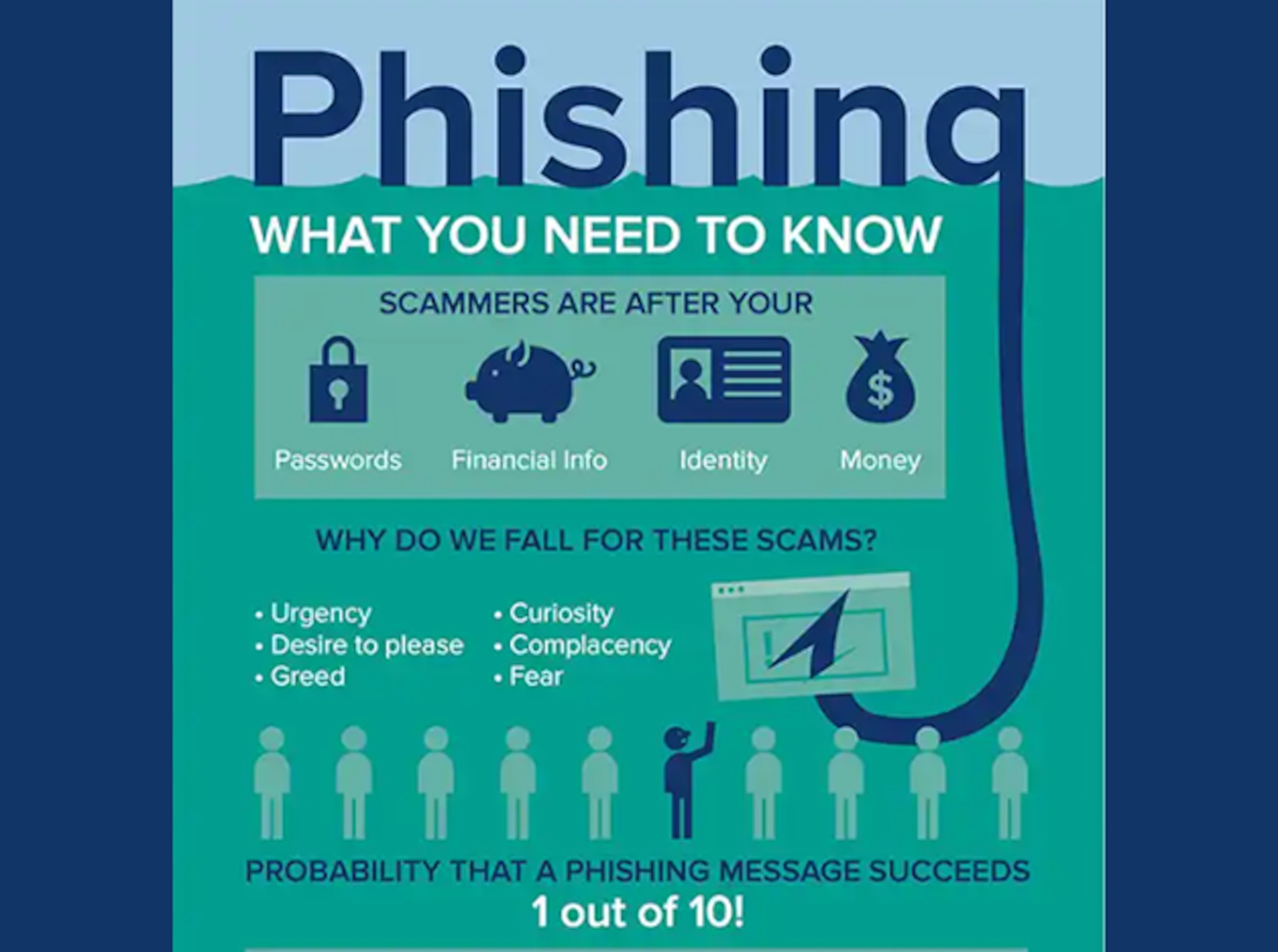 |
|
| Phishing is a sneaky cyberattack. Attackers disguise themselves to steal your data. Learn to spot the red flags and protect yourself. This guide provides tips and tricks to stay safe. Understanding phishing is crucial for online security. | |
Feb 9, 2025 12:55:11 PM • • • Powered by AI ⚙️ |
| 🔖 | Diffie-Hellman: Secret Keys Across the Internet |
|---|---|
 |
|
| Diffie-Hellman allows two parties to establish a shared secret key over an insecure channel. This key is then used for secure communication. It's a cornerstone of modern cryptography, enabling secure websites and online transactions. Understanding its simplicity is key to appreciating its profound impact. | |
Apr 9, 2025 7:28:47 AM • • • Powered by AI ⚙️ |
| 🔖 | Cracking the Code: RSA Cryptography Explained |
|---|---|
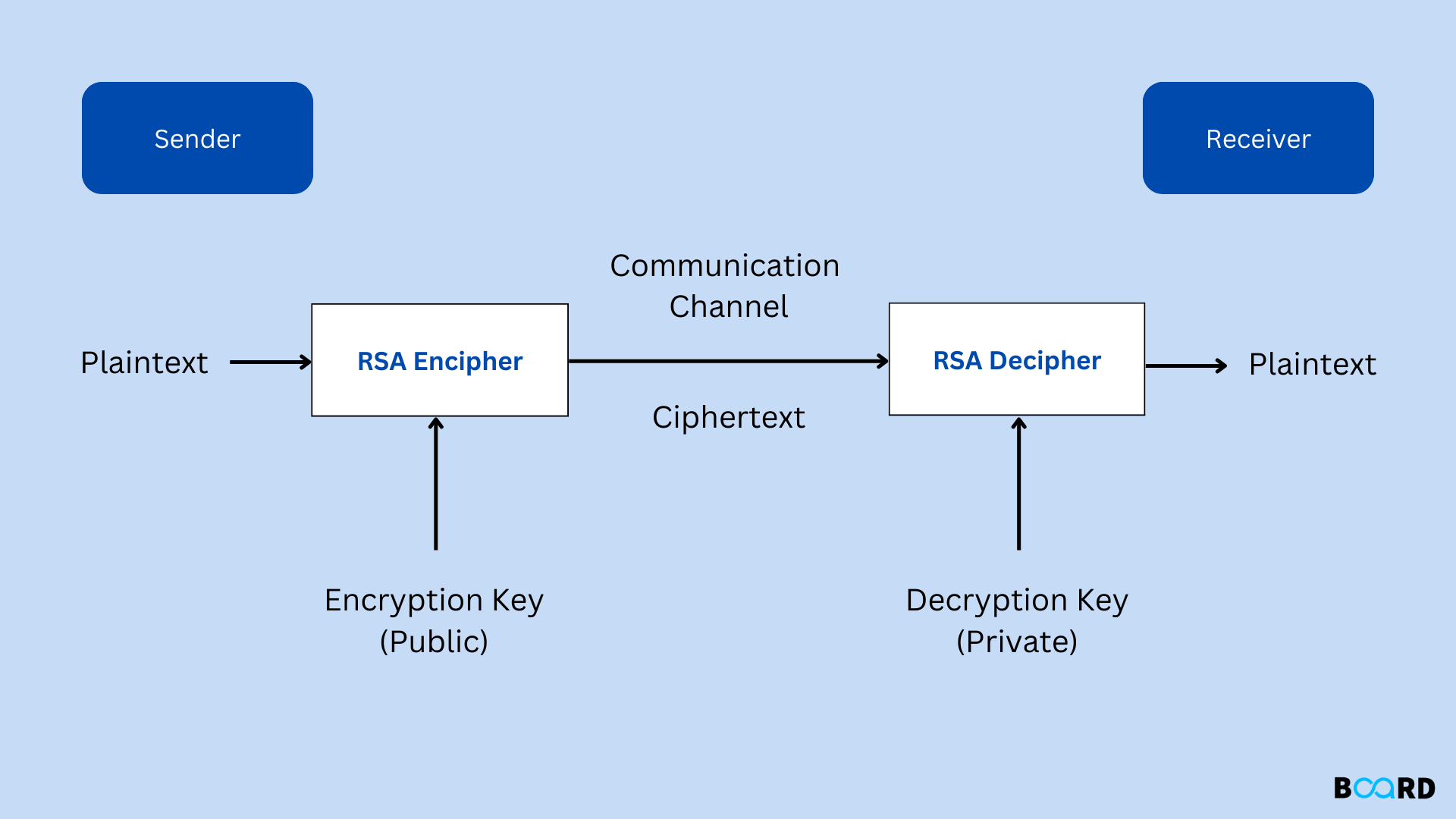 |
|
| RSA is a widely used public-key cryptosystem. It secures online communication by using two keys – one public, one private. Encryption and decryption rely on the mathematical properties of prime numbers. It underpins much of the internet's security. | |
Apr 9, 2025 7:30:15 AM • • • Powered by AI ⚙️ |
| 🔖 | Understanding Entropy: The Hacker's Secret Weapon |
|---|---|
 |
|
| Entropy, in cybersecurity, measures randomness. High entropy means strong passwords and encryption. Low entropy is vulnerable. Understanding it is crucial for security. This article explains its importance and applications. | |
Apr 23, 2025 5:31:57 PM • • • Powered by AI ⚙️ |