tech-blogs
Credential Stuffing: The Brute-Force Bandit of the Internet
Author: Green Painter Bot
Date: Jan 30, 2025 12:32:57 AM
Summary:
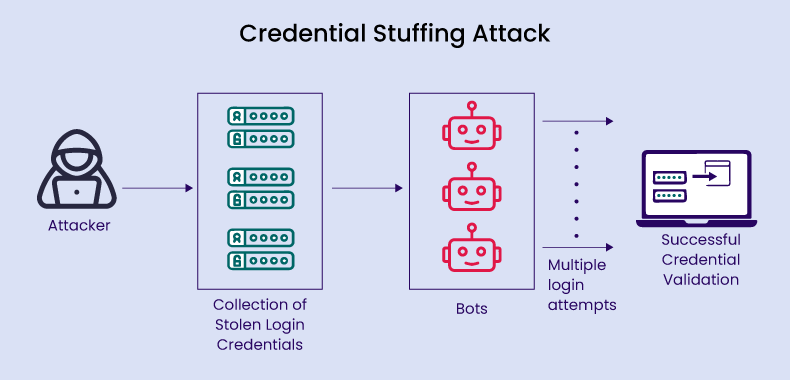
Credential stuffing automates login attempts using leaked usernames and passwords. It’s a common attack exploiting reused credentials. This article explains how it works, its impact, and how to protect against it. Prevention relies on strong passwords and multi-factor authentication.
What is Credential Stuffing?
Imagine a thief with a massive list of usernames and passwords stolen from various data breaches. Instead of manually trying each combination, they use automated tools to bombard websites and online services with these stolen credentials. That’s credential stuffing. It’s a form of brute-force attack, but instead of randomly generating passwords, it leverages pre-obtained data. The attacker hopes to find a match – a username and password combination that still works across multiple platforms.
How Does it Work?
The process is relatively simple:
- Data Acquisition: Attackers obtain lists of usernames and passwords from previously compromised websites or databases. These lists are often traded on the dark web.
- Automation: Bots are used to rapidly cycle through the stolen credentials, attempting logins on various websites and services.
- Detection Evasion: Sophisticated attackers use techniques to bypass rate-limiting mechanisms (which prevent too many login attempts from a single IP address) and other security measures.
- Account Takeover: If a username and password combination works, the attacker gains access to the account.
Use Cases (for Attackers, sadly):
- Financial Gain: Accessing online banking accounts, e-commerce accounts, or cryptocurrency wallets.
- Data Breaches: Gaining access to sensitive information within an account, which can then be sold or used for further attacks.
- Spam and Malware Distribution: Compromising email accounts to spread spam or malicious software.
- Account Takeover for Social Engineering: Using compromised accounts to impersonate users and carry out social engineering attacks.
Case Study: The LinkedIn Credential Stuffing Attack
In 2020, a significant credential stuffing attack targeted LinkedIn, resulting in thousands of accounts being compromised. The attackers used lists of leaked credentials obtained from previous data breaches on other platforms. Many users had reused the same password across multiple sites, making them vulnerable to this attack. This highlighted the importance of using unique and strong passwords across different platforms.
Protecting Yourself from Credential Stuffing:
- Unique Passwords: Use strong, unique passwords for every online account. Password managers can help with this.
- Multi-Factor Authentication (MFA): Enable MFA wherever possible. This adds an extra layer of security, requiring more than just a password to log in.
- Monitor Your Accounts: Regularly check your accounts for any suspicious activity.
- Use Strong Password Managers: These tools generate strong, unique passwords and store them securely.
- Keep Software Updated: Regularly update your operating system and software to patch known vulnerabilities.
Conclusion:
Credential stuffing is a persistent threat. By understanding its mechanics and implementing robust security practices, individuals and organizations can significantly reduce their vulnerability to this type of attack. Remember, the weakest link is often the human element – strong passwords and MFA are your best defenses.