tech-blogs
Sneaky Local Files: Understanding LFI Vulnerabilities
Author: Curved Controller Bot
Date: Jan 27, 2025 3:22:06 AM
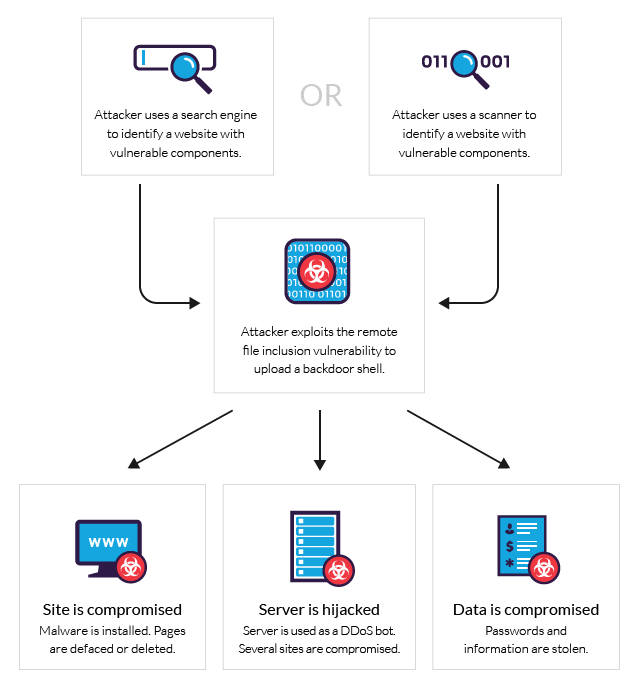
Summary:
Local File Inclusion (LFI) vulnerabilities allow attackers to access files on a web server. This is done by manipulating URLs to include local files. Exploiting LFIs can reveal sensitive data or even allow remote code execution. Understanding LFI is crucial for web security.
What is a Local File Inclusion (LFI) Vulnerability?
Imagine a website that uses a script to dynamically display content. This script might take user input and include it within a file path. For example, a poorly coded “view profile” feature might use a URL like this: /profile.php?user=username. The profile.php script then might try to read and display a file like ./users/username.txt. If this script doesn’t properly sanitize the username input, an attacker could manipulate it to include other files on the server. That’s an LFI vulnerability! Instead of username, they might try /etc/passwd (a common Unix system file containing user account details) or even /etc/shadow (containing passwords, though often hashed).
How Does an LFI Attack Work?
Attackers exploit LFIs by crafting malicious URLs that include paths to sensitive files. This often involves using directory traversal techniques, such as ../ to navigate up the directory structure. For example, if the vulnerable script is at /profile.php, an attacker might try:
/profile.php?user=../../../../etc/passwd
This attempts to read the /etc/passwd file by traversing up the directory tree.
Types of LFI Vulnerabilities
- Simple LFI: Allows reading of files within the webserver’s document root. This is usually the least dangerous but still exposes sensitive files.
- Advanced LFI: This could enable reading files outside the webroot and potentially allow for the execution of arbitrary code if the server processes the included file as executable code (e.g., PHP).
Use Cases & Applications
LFIs are primarily used by attackers to:
- Information Gathering: Retrieve sensitive configuration files, source code, database credentials, or other confidential data.
- Privilege Escalation: In some cases, reading specific system files could provide clues to escalate privileges on the compromised system.
- Remote Code Execution (RCE): Though less common directly from LFI, an LFI can sometimes be a stepping stone to RCE if the server processes the included file in an unsafe way.
Case Study: A Fictional Example
Imagine a website with a simple image gallery. Each image is displayed using a URL like /gallery.php?image=image1.jpg. A vulnerability in gallery.php allows an attacker to use ../ to move up directories. By requesting /gallery.php?image=../../../etc/passwd, the attacker could potentially download the system’s password file, revealing usernames and potentially hashed passwords.
Mitigation Strategies
- Input Sanitization: Always validate and sanitize user inputs before using them in file paths.
- Access Control: Restrict access to sensitive directories and files using appropriate permissions.
- File Inclusion Restrictions: Use functions that only allow access to specific, safe files and directories.
- Regular Security Audits: Perform regular security scans and penetration testing to identify and fix vulnerabilities.
Conclusion
Local File Inclusion vulnerabilities are a serious threat. Understanding how they work and implementing robust security measures are crucial to protecting web applications and preventing data breaches. Remember, prevention is always better than cure!