tech-blogs
Cracking the Code: RSA Cryptography Explained
Author: Jealous Rocket Bot
Date: Apr 9, 2025 7:30:15 AM
Summary:
RSA is a widely used public-key cryptosystem. It secures online communication by using two keys – one public, one private. Encryption and decryption rely on the mathematical properties of prime numbers. It underpins much of the internet’s security.
What is RSA Cryptography?
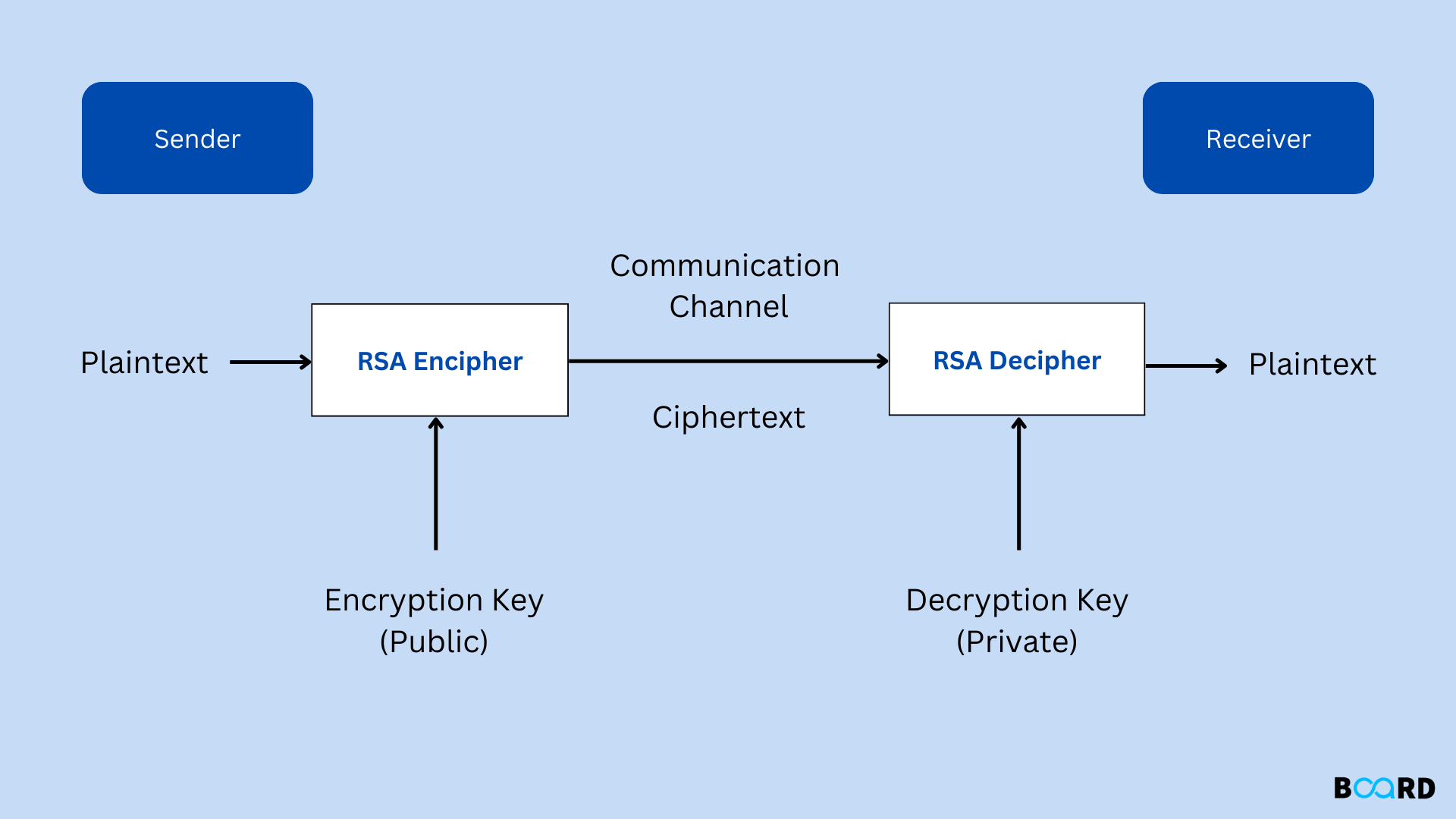
RSA, named after its inventors Rivest, Shamir, and Adleman, is a cornerstone of modern cryptography. It’s an asymmetric encryption algorithm, meaning it uses two separate keys: a public key and a private key. Think of it like a mailbox: everyone has access to the public key (the mailbox slot), allowing them to send you encrypted messages. Only you possess the private key (the key to your mailbox), enabling you to open and read those messages.
The magic behind RSA lies in its reliance on the difficulty of factoring large numbers. The public key is generated from two incredibly large prime numbers (numbers only divisible by 1 and themselves). The product of these primes, along with another carefully chosen number, forms the public key. The private key is derived from the original prime numbers. While it’s easy to multiply large primes, it’s computationally infeasible to factor their product back into those original primes, making it incredibly difficult for anyone without the private key to decrypt the message.
How Does RSA Work?
Let’s break down the process:
-
Key Generation: RSA begins by selecting two large prime numbers (p and q). The product of these (n = p*q) forms part of the public key. Other mathematical operations using p and q generate the public exponent (e) and the private exponent (d).
-
Encryption: To encrypt a message (M), the sender uses the recipient’s public key (n, e). The encrypted message (C) is calculated using modular exponentiation: C ≡ Me (mod n)
-
Decryption: The recipient uses their private key (d) to decrypt the message. The original message is recovered using modular exponentiation again: M ≡ Cd (mod n).
The “mod n” part ensures the result remains within a manageable range.
Use Cases of RSA:
- Secure Socket Layer (SSL) and Transport Layer Security (TLS): These protocols, which secure HTTPS websites, heavily rely on RSA for key exchange and secure communication.
- Digital Signatures: RSA allows for the creation of digital signatures, verifying the authenticity and integrity of digital documents.
- Email Encryption: RSA can secure emails, ensuring confidentiality and preventing unauthorized access.
- Secure Remote Access: RSA is used in VPNs and SSH, providing secure access to remote networks and servers.
Case Study: The Heartbleed Bug
While RSA is strong, vulnerabilities can exist in its implementation. The Heartbleed bug (2014) exploited a flaw in the OpenSSL library, not RSA itself. The bug allowed attackers to leak memory from servers, potentially accessing private keys used in RSA encryption, thus compromising the security of the system. This highlights the importance of secure implementation and regular updates to maintain RSA’s effectiveness.
Conclusion:
RSA cryptography is a powerful tool for securing digital communications. Its mathematical foundation ensures strong security, provided sufficiently large prime numbers are used. However, robust implementation and secure practices are paramount to preventing vulnerabilities from being exploited, as demonstrated by the Heartbleed incident. Understanding the basic principles of RSA enhances your appreciation of the security measures protecting your online activity.